Manufacturing Industry
Protect your production line and operations through superior threat detection.
Manufacturers are in the top five most targeted industries for cyberattacks, with intellectual property and financial gain at stake for threat actors. Security professionals who work for manufacturing organizations often jugge multiple priorities while trying to keep their organization protected. Staying up-to-date on patches, reviewing access levels and investigating incidents are just a few responsibilities under the security umbrella. With plants in other countries, and in multiple time zones, security for manufacturing is not an 8-to-5 job. It requires a 24/7/365 staff that can monitor for threats at any hour of the day.
Binary Defense can help shield your manufacturing business from cyberattacks, ensuring attacks are detected within minutes. You will have peace of mind knowing that our Security Operations Task Force is watching around the clock for abnormal behaviors on your network
Get in Touch
Learn more about our solutions for manufacturers.
MORE RESOURCES
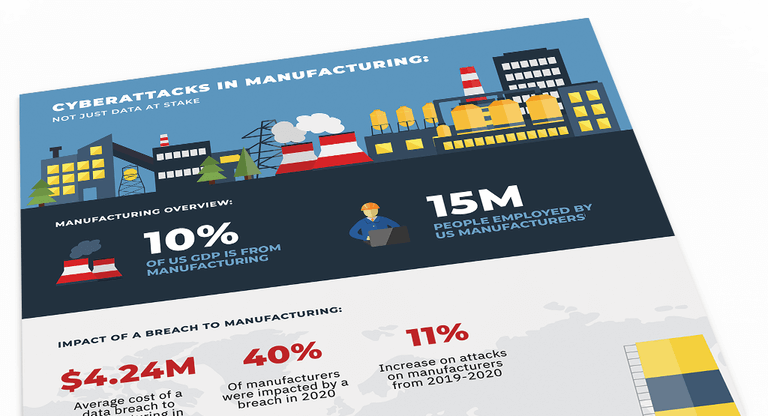
Cyberattacks In Manufacturing: Not Just Data At Stake
If a manufacturer is hit with a cyberattack, what is the impact to operations and intellectual property? How can a manufacturer stay safe?
Protect Against Ransomware and Other Attacks
The manufacturing industry is among the top five most highly-targeted industries for a ransomware attack, according to TechRepublic. What’s more, many manufacturers don’t have dedicated security personnel. Protect your operations from ransomware with industry-leading technology and service that watches over you 24/7/365.
Our Solutions
What do our partners have to say?
MORE RESOURCES
Threat Hunter finds renamed system utilities by file hash to uncover multiple attacks
Summary: Threat hunting is a vital but often misunderstood practice for organizations and security teams. Curiosity is one of the driving forces behind any…