We recently became aware (special thanks to @slideintohome) of a SMTP botnet campaign occurring for a number of large-scale customers targeting SMTP gateways with Shellshock based attacks. The attack leverages Shellshock (https://www.trustedsec.com/september-2014/cve-2014-6271/) as a main attack vector through the subject, body, to, from fields (targets every main header field in order to download the perl botnet script). Once compromised, a perl botnet is activated and beaconing on IRC for further instructions.
Below is the original email sent containing the initial ShellShock payload:
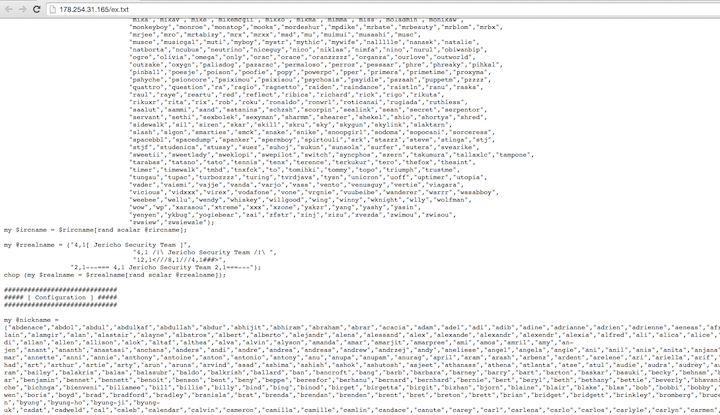
The curl/wget/fetch/perl/lwp/etc methods are attempting to pull down a perl based botnet from the Jericho Security Team in order to infect the SMTP gateway and add it to an existing botnet infrastructure. Visiting the site, we can see the relevant source code from the malicious website:
It’s unknown which product would specifically be vulnerable to this since Shellshock relies on system level calls and leveraging bash however it seems to be a fairly wide-scale delivery of emails across the United States. We continue to see Shellshock attempts actively being exploited in the wild since it was disclosed in September. We recommend that organizations ensure any systems utilizing bash should already be patched or should be immediately.Binary Defense customers are already actively blocking these attackers since it’s detection and notification process.