Microsoft’s Azure App Service recently patched a security flaw dubbed “NotLegit” which allows public access for Local Git repositories. This means that proprietary or sensitive source code written for applications in Java, Node, PHP, Python, and Ruby – i.e., deployed to “Local Git” in Azure App Service since September 2017 or deployed to Azure App Service since September 2017 using any Git source — have been accessible to attackers since September 2017 when Azure App Service was first made available, because they do not utilize web servers that support web.config files. Azure App Service uses such web.config files to block public access to the associated directories. Applications written in C# and ASP.NET that employ the Microsoft IIS webserver are not affected due to default use of web.config files which work as intended to block access to the copy of the .git folder stored in /home/site/wwwroot.
The flaw was discovered by the Wiz Research Team and reported to Microsoft on October 7th, 2021. Microsoft has issued a mitigation for most Azure App Service customers but some customers have configurations that remain vulnerable. Microsoft stated all such customers should have received emails detailing details of mitigation between December 7th and 15th. A sample email from the Wiz blog with Microsoft recommendations is below:
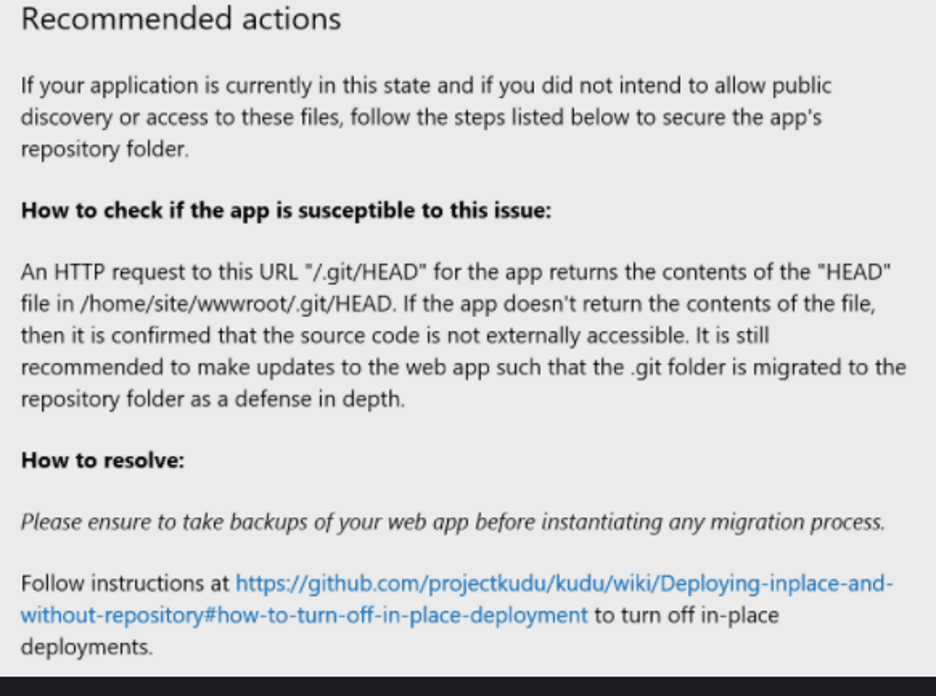
Analyst Notes
Randy Pargman, VP of Threat Hunting and Counterintelligence for Binary Defense, commented that “This is significant for security practitioners.” Pargman says attackers can use the source code to exploit the service or find hidden vulnerabilities in the website. “No secrets or API keys should be stored in the code, but instead should be referenced from environment variables or secure key stores,” he says. While many website developers embed API keys and secrets in the source code because it’s faster and easier, if an attacker gets those keys, “they can do anything that the API allows.”
The Wiz Research Team has already noted it has found multiple attempts to exploit this vulnerability in its honeypots within a week of setup, prior to public disclosure, and therefore believes such attempts are regularly part of tactics used in the wild.
https://www.govinfosecurity.com/azure-app-services-flaw-exposed-source-code-for-4-years-a-18207
https://blog.wiz.io/azure-app-service-source-code-leak/
