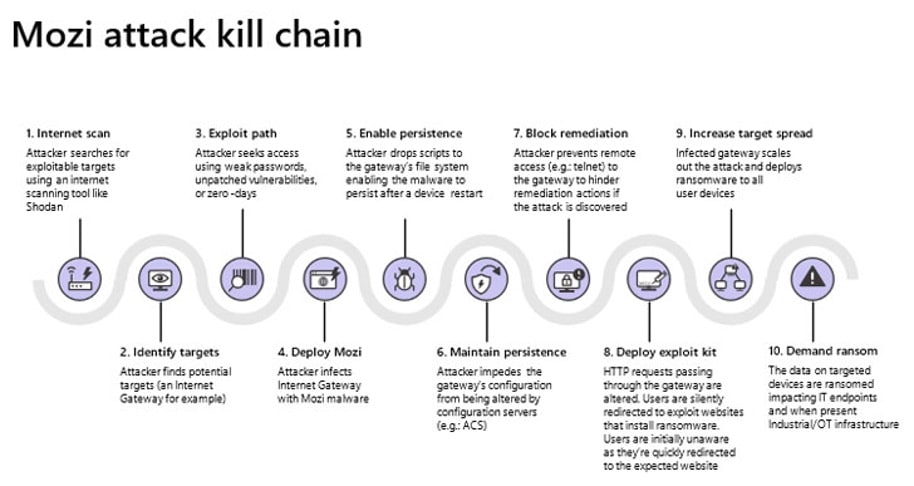
New information has revealed that the Mozi botnet now has the capabilities to achieve persistence in Netgear, Huawei, and ZTE network gateways. Microsoft Security Threat Intelligence Center and Section 52 at Azure Defender for IoT have been observing the botnet and in a technical write-up they stated, “By infecting routers, they can perform man-in-the-middle (MITM) attacks—via HTTP hijacking and DNS spoofing—to compromise endpoints and deploy ransomware or cause safety incidents in OT facilities.” While the malware used to have a different course of action during infection, it now takes specific actions to increase its chances of survival upon reboot or any other attempt by other malware or responders to interfere with its operation.” Along with persistence allowing it to stay active on the network it can hijack computer sessions and re-route traffic to a domain run by attacks via DNS spoofing. The model below shows Mozi’s “Attack Kill Chain”:
Analyst Notes
It has been advised that users of Netgear, Huawei, and ZTE routers should change passwords and make them strong and not the same as previously used passwords. Updates to the devices should be implemented as soon as they are available to avoid the risk of any vulnerabilities being exploited.
https://thehackernews.com/2021/08/mozi-iot-botnet-now-also-targets.html?web_view=true&m=1
