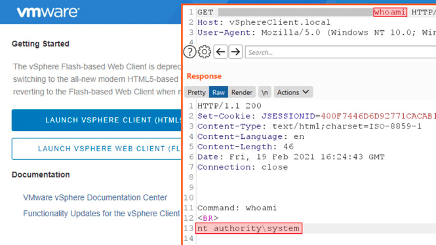
VMware issued a security advisory on February 23rd for multiple vulnerabilities, including CVE-2021-21972, an unauthenticated remote code execution (RCE) vulnerability in VMware vCenter. The flaw was found by Mikhail Klyuchnikov of Positive Technologies. Few details have been given about the vulnerability until administrators have had time to update. According to the security advisory, the issue lies within the HTML5 client for a vCenter Server plugin. Anyone with access to port 443 to the server can issue commands to the host system with “unrestricted privileges”. VMware has given this this vulnerability a CVSSv3 score of 9.8 out of 10, a Critical severity rating. As of this writing, over 6700 vCenter servers could be found that were accessible directly from the Internet.
Analyst Notes
CVE-2021-21972 has been given a Critical severity rating. Binary Defense highly recommends all administrators visit the VMware security advisory to apply the update specific to their version of vCenter. Binary Defense also recommends evaluating whether these servers need to be exposed directly to the Internet. Placing services that don’t need to be accessible to the general public behind a VPN offers an extra layer of security and can reduce a malicious actor’s initial attack vector. It is likely that threat actors are already busy collecting a list of IP addresses of publicly-exposed vCenter servers—as soon as an exploit to this vulnerability is available, they will likely race to be the first to exploit the servers and take as much information as they can get.
Source: https://twitter.com/ptswarm/status/1364283310281785350
https://www.vmware.com/security/advisories/VMSA-2021-0002.html
